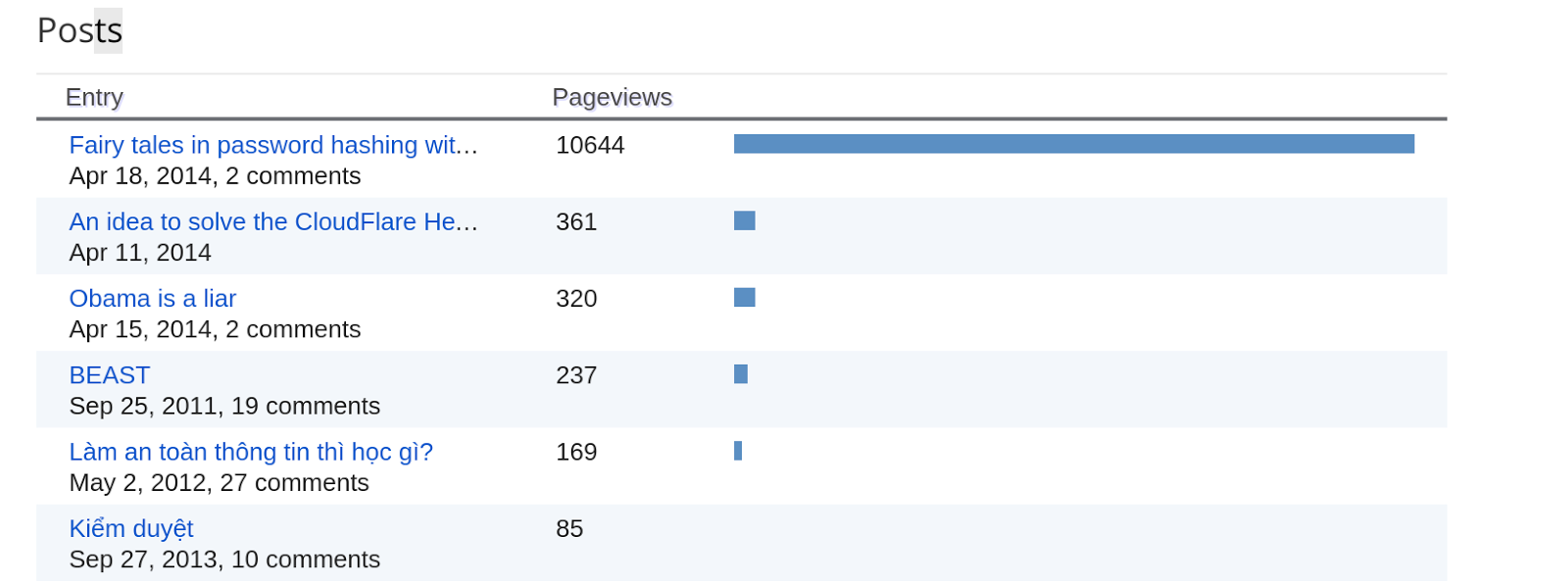
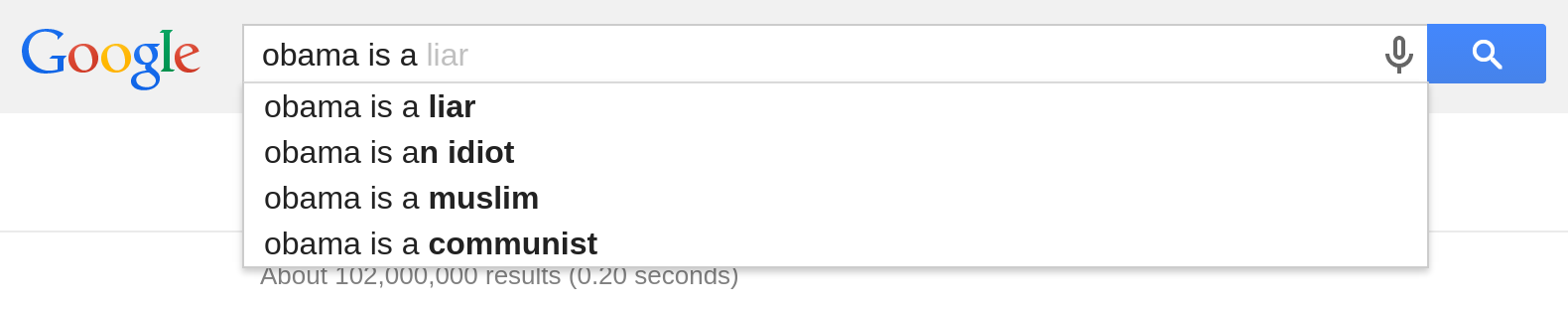
Theo Google, một công ty của Mỹ, thì đương kim tổng thống Mỹ là một thằng nói láo, ngu dốt, theo đạo Hồi và cả cộng sản. Mà Google chỉ là dựa vào gợi ý của người dùng Internet thôi nhé: đây là những cụm từ xuất hiện nhiều nhất khi người ta muốn mô tả Obama. Không tin thì bạn thử tìm đi. Thấy chưa? Thấy dân Mỹ chửi Obama như chửi con chưa? Thế mà chẳng thấy ai bị bắt gì cả. Lăng mạ như thế này thì còn thể thống gì nữa. Tự do mà không có khuôn khổ thế này thì loạn mất. Thế mà nước Mỹ vẫn ổn, vẫn giàu mạnh. Một trăm năm mươi năm nay chuyển giao quyền lực không hề đổ một giọt máu, chỉ có tốn nước miếng thôi. Trong lúc đó... có một ông tên là Trương Duy Nhất viết blog nói về các "Obama của Việt Nam", chưa dám chửi như chửi con, cũng chẳng dám mắng như chủ mắng đầy tớ, chỉ mới nói nhẹ vài tiếng, nhưng cũng đã được tặng vài cuốn lịch xé chơi q...